Global Warming: What are the practical steps that can help in reducing Global Warming?
September 15, 2022
The Impact of FDI on Economic Growth in The UK
September 18, 2022The study looks at how social media censorship in the UAE affects young people's freedom to express themselves online. It explores how rules on the internet can impact what young folks can see and say on platforms like Instagram and Twitter.
Introduction
The Internet is a staple of the modern world, one that contemporary humans use to increase the overall level of communication among them. The widespread availability and progressively decreasing costs of internet access have rendered it increasingly attractive with time.
Learn More about Social Media Dissertation Topics
Meanwhile, while social media platforms are an important component of the Internet, as they are digital mirrors of physical communication and interaction, they differ in that they offer the capability of sharing and communicating on a whole new level. The option to use digital data that consists of audio, images, videos, text, etc. makes the social media platforms a very attractive and widely used part of the Internet. However, the use of social media is not seen in positive terms by all societies and countries. Indeed, there are a significant number of people who hold the belief that the Internet should be censored and controlled in variable magnitude. The reasons for this vary among different groups and individuals (Loader, Vromen, and Xenos, 2014).
Aims
For a dissertation to be effective, it needs to have specific aims that it hopes to achieve. This dissertation has the following aims, which were alluded to in the previous sub-section:
- To examine the extent of social media censorship in the United Arab Emirates.
- To investigate how young people are affected by social media censorship in the United Arab Emirates.
- To examine the perceptions of young people on social media censorship.
Background
This sub-section provides the general background to the topic in question.
Background information serves to provide the reader with the appropriate contextual background knowledge that is intended to give them a basic understanding of the topic, presenting pertinent information that allows them to become familiarised with it. The process of creating a background of information about any given topic can facilitate a scholar’s accurate and precise navigation around the different ideas and aspects of it, as the scholar will essentially have ‘the lay of the land. The background is also useful for laying out general and specific information given connecting the topic with the larger subject at hand and providing a contextual link for the generation of an enhanced relationship between the two.
Members of the society, as a whole, impose a particular set of standards on each other that they deem necessary for their maintenance and propagation. These standards can be set into two distinct categories based on their specific characteristics: internal standards and external standards. External standards are generally referred to as ethics and are the standards that members of society collectively impose on each other. Breaking away from these standards has the potential to expose the offending party to several detrimental outcomes that may vary in severity based on the extent of the violation as well as the standards of conduct followed by society as a whole. Meanwhile, internal standards are generally described in terms of morals and are personally held beliefs that can arise from the self or can be commonly attributed to a higher power, such as God. In short, they are the inherent values that an individual holds (Russell, 2013).
Ethics can be considered to be a product of morals, as they tend to be derived from the beliefs and values of a collection of individuals who use them to establish their standards for interacting with each other. Each country around the world is composed of different people who grow up in diverse backgrounds and are subjected to varying conditions. As a consequence, the ethics and morals they hold will be considerably different. The United Arab Emirates (UAE), the nation chosen for this dissertation, is a country in which the intrinsic standards are based on the religion of Islam. Most of the country’s (native) population is comprised of Muslims, whose values are derived from the ethics and morals of Islam. Compared to similar-scale value-based societies, the UAE can be described as a more conservative society with elements of liberalism mixed in it, while it remains a predominantly conservative society (Deneulin, 2014).
With this, the nation’s government believes that the information and media to which the country’s residents are exposed can have a significant number of detrimental effects and outcomes. This does not simply entail a utilitarian approach designed to improve the personal development of human beings but is also deeply rooted in religious beliefs. According to their interpretation, these religious beliefs describe freedom of information as posing a threat. Certain topics or subjects hold a very controversial position, and, in general, anything associated with sin or wrongdoing must, according to the authorities, be censored. This is largely focused on the data to which the country’s young people are exposed, as the government believes in providing a tailored online experience that removes elements of what they perceive as ‘bad’ or ‘evil’ (Katzman, 2010).
Since social media plays an enormous role in the lives of young people in the country, it has been decided by the government that it must be heavily tailored and customized to reduce the dissemination of unwanted or harmful material. The rapid penetration and evolution of information technology have seen internet access increase around the globe, and the United Arab Emirates (UAE) is no exception to this (Al-Jenaibi, 2011). The country is considered to be one of the most connected states, based on the statistics released by the International Telecommunication Union in 2016, which demonstrated that it has a 91 percent internet penetration. By 2017, there were over a million internet subscribers (Dennis, Martin, and Wood, 2016). Among Emiratis, many individuals, especially the youth, utilize social networking sites (SNSs) to communicate with their friends, family members, and others. In fact, on average, Emiratis spend approximately 2.56 hours a day on social media (Freedom House, 2018), which has been largely attributed to social media becoming a vital part of everyday life.
Social networking sites, such as YouTube, Twitter, Instagram, and Facebook, are known as web-based communities that offer ideal platforms for individuals, groups, and entities to create content, share interests, information, and ideas, and interact socially by connecting with various users (Al-Jenaibi, 2011). Nonetheless, the potential of the Internet to enhance free expression is not definitively welcomed on a global level.
Indeed, in dictatorial regimes, social media is tightly regulated through a vast array of means. Much like other Arab and Islamic nations, the UAE is perceived as a country with an ingrained Islamic culture whereby culture and religion guide the societal norms (Martin et al., 2018). Consequently, courtesy of religious and societal customs, communications are somewhat limited. Indeed, the UAE’s telecommunications industry is tightly controlled by the state, which regulates the two major service providers in the nation.
The close connections between telecommunication entities and the government have resulted in the censorship of Voice-over-IP (VoIP) (Shishkina and Issaev, 2018). In 2017, internet freedom was largely restricted due to the implementation of the cybercrime regulations, which was followed by the imprisonment of various personalities who had been using social media for political expression, including Nasser bin Ghaith, a human rights defender, who received a 10-year sentence (Shishkina and Issaev, 2018). Subsequently, while the nation was ranked highly among the Arab States in terms of information communication technology (ICT), its development fell slightly (Dennis, Martin, and Wood, 2016). Furthermore, the government restricts access to religious, political, and social content, which includes gambling, pornography, and political discussions. Several researchers have examined internet censorship, including in terms of people's attitudes towards it (John and Chung, 2016).
Rationale
The presentation of information plays a vital role in the contemporary world, as the information an individual can access determines, to a large degree, their overall perspectives and worldview. The censorship of information and social media thus represents a factor that can have far-reaching consequences. Exploring this phenomenon is, therefore, a pertinent requirement, as it can allow for the observation of the effects that such practices can have on an individual and society as a whole. The increased access to information and social interaction online, or the lack of it, can be analyzed in terms of the attendant effects, both short- and long-term.
Outline
This sub-section provides an outline of the entire paper. It provides a brief overview of the chapters that follow in addition to each chapter’s specific purpose. This allows for this sub-section to serve as a signpost for the entire dissertation, such that the essence of the information that is presented therein can be quickly scanned and analyzed without the need to undertake a lengthy amount of reading.
The first chapter, which includes this sub-section, introduces the topic on which the dissertation is focused. It highlights the main aims that the author hopes to achieve through this exercise and the objectives that are derived from them. These objectives demonstrate the discrete tasks that need to be undertaken to achieve the aforementioned aims. The background presents pertinent background information within the direct context of the topic. This information is useful for generating context and providing an overview of the subject area being discussed as well as some real-world context. Finally, the section on ethical considerations presents any ethical factors that may have to be taken into account such that standard ethical practices are observed.
The second chapter consists of a literature review. The literature review teaches the work of other scholars by retrieving it from electronic databases for analysis and discussion. This provides additional context surrounding the subject and presents the work that has already been conducted in the chosen subject area or field of study. It also reduces the level of redundancy in terms of avoiding any repetition of what has already been conducted.
The third chapter addresses the methodology. It describes the approach taken to undertake this dissertation. In addition to a description of the methods employed, their usage is justified through the appropriate use of analysis and discussion in terms of why the specific research methodology was chosen and why it presents the best approach for this dissertation. The tools for analysis are also presented alongside the limitations that may be presented by the chosen approach.
The fourth chapter lays out the data and information that were extracted as a result of the efforts undertaken in the previous section. This section restricts its focus to a simple presentation of the information and there is no consideration of its implications, nor is there any attendant discussion. In short, this chapter purely consists of outlining the data that is used for analysis in the following chapter.
The fifth chapter discusses the data presented in the previous chapter. The data gathered is examined in the context of where it lies in the general background area of the subject. The interpretation of and any meaning that can be derived from the data is explored in this chapter. This information is then further used in the next chapter, the concluding chapter of the dissertation.
The sixth and final chapter concludes the entire work by presenting a summary of what was presented in the preceding chapters. The key findings identified through the research are highlighted, as this allows for demonstrating the importance of the valuable data that were retrieved through the research efforts. The social and academic contribution made by this dissertation is also briefly analyzed and discussed, followed by a presentation of the limitations of the study. These limitations not only define the shortcomings of the study but also specify the parameters under which the data and knowledge generated by this study fall. Finally, a recommendation sub-section is presented, which includes a list of recommendations that future scholars can follow to guide them in their research endeavors.
Ethical Considerations
This sub-section of the paper consists of the ethical considerations that had to be examined before the study could continue. Ethics are guidelines and rules that dictate right and wrong conduct and are collectively imposed by society as a whole on each of its members. It is through this collective decision that humans decide on what can be considered an acceptable standard of conduct, that is, what is considered to be good, and what is considered to be bad. The ethical standards upheld at the time of writing demand that the ethical considerations be addressed before any research study can be launched. As a result, to comply with the standards and regulations, ethics must be considered a significant component of this dissertation (Connelly, 2014).
The research design and framework dictate the aspects of ethics that need to be addressed. Addressing these concerns is crucial, and best practice dictates that a thorough analysis of all the potential ethical factors has been conducted. This allows for the alleviation of any potential ethical concerns, or, at the very least, it allows for steps to be taken to minimize the number of ethical transgressions that may occur. As this research utilizes both primary and secondary approaches, several ethical considerations had to be addressed, especially in terms of the primary data collection method (Miller et al., 2012).
Here, the aspect of social responsibility is a prominent factor, as research should be geared towards maximizing the benefits to society while minimizing any potential harm that could arise and providing support and assistance to those in need. This research does not represent a major threat to society in general, as will be proven through the points that follow. Impartiality is an important aspect that the author strived to maintain throughout this research, which has no external funding or sources that may provide a conflict of interest. All the participants involved in the primary research were approached beforehand, and their informed consent was obtained before the data collection method was applied. Nonetheless, due to the sensitive nature of the topic in certain places, the information received may prove dangerous or detrimental to some of the participants (Resnik, 2011). Thus, to ensure the safety of the participants by obviating any detrimental effects, specifically identifiable data was stripped from this dissertation such that no information that could be used to uniquely identify a participant is presented therein. Only the meta-data, which are non-identity specific and cannot be used to identify individuals, are included. To ensure full integrity and transparency in the research, all the steps undertaken in this exercise are documented, while no datum, fact, or any other piece of relevant information is omitted. This ensured that everything was recorded and documented such that any potential problem, conundrum, shortcoming, or other discrepancy or issue could be identified and addressed as necessary (Vainio, 2013).
The secondary approach of this dissertation is concerned with data collection using electronic databases to retrieve scholarly articles about the subject for review and analysis. While there would appear to be no major concerns associated with secondary research approaches, it is nonetheless important to consider the type of information that is to be addressed as well as the topics or subjects that are to be explored. This is because certain subject areas are in a state of delicacy in which they are considered to be sensitive issues by society as a whole, which creates a large amount of emotional baggage that may have its roots in general ignorance, intolerance, or in unknown factors that are connected to or entrenched in it. Overall, it has been determined that this research represents no significant source of issues or danger for the author (Neuman and Robson, 2014).
The following texts are related to the literature review of the study.
Literature Review
A literature review is an important part of any dissertation, as it allows the author to draw upon the work of other scholars who have conducted studies and investigations related to the same subject matter. This holds multiple benefits for both the author and the scholarly community associated with studying the subject. The author benefits from having access to previous work completed in the subject area, which allows them to glean what information is available on the subject already, helping them to direct their research by using the previous studies as a guide. Furthermore, the redundancy of research is minimized, as the author will be able to bypass any endeavors that have already been accomplished. The research of the author can also be placed within the context of the other works, providing a further piece of the puzzle which is the overall image of the subject (Galvan and Galvan, 2017). Meanwhile, the author can identify any existing gaps in the literature before either using these gaps as a guide in his or her study or simply identifying them as problems that other scholars may choose to alleviate.
This chapter of the dissertation is focused on conducting a literature review by examining the relevant research articles of other scholars. Two sources are available in terms of conducting this literature review. The first source is physical databases, which consist of data that are present in physical material and need to be sorted through manually. This presents an arduous task, as physical databases are not only cumbersome due to the volume of space they occupy, but also entail the inconvenience of browsing through potentially thousands of files to locate the relevant data. In addition, obtaining direct access to the databases of the UAE presented a problematic factor, as this project does not have the resources required to undertake such an endeavor. It is under these circumstances that the decision was taken to exclude the usage of physical databases entirely from this review (Fink, 2019).
Digital databases consist of archives where information is stored in digital format.
Digital databases hold a large number of research articles that can be browsed for pieces of work that directly relate to the research subject. Digital databases offer several advantages that make them a preferable option over physical databases. For one, they offer the possibility of sorting through a large number of files using a computer, which means this feat can be accomplished in a matter of seconds, compared to potentially hours of manually sorting through files in a physical database. Sorting through digital databases is also a more pleasant task, as each article will be tagged with a particular set of keywords that directly relate to the subject in question.
Thus, retrieving the relevant articles was conducted through the use of specific keywords. The results returned then underwent a process of sorting and filtering (McMenemy, 2012).
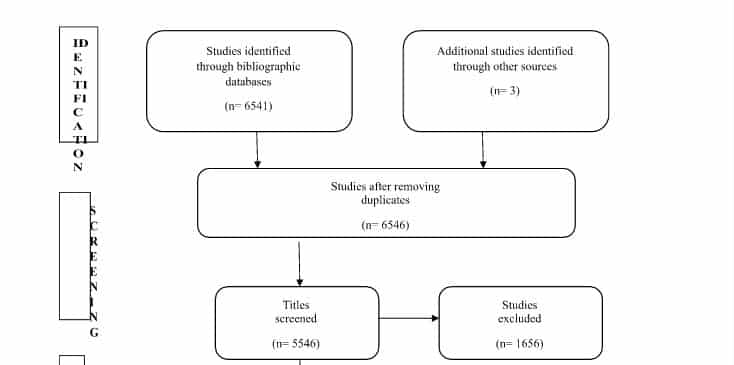
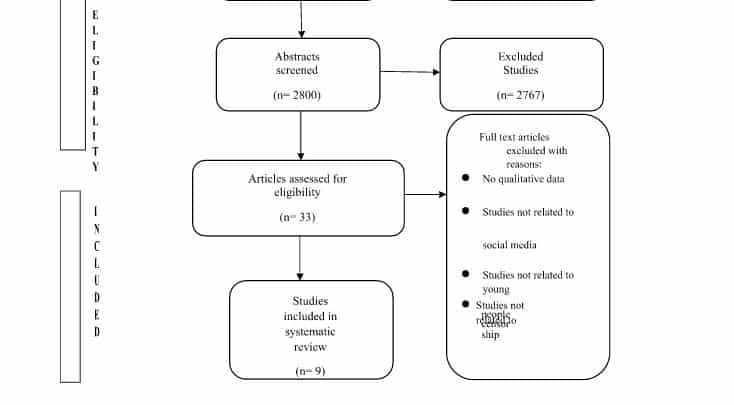
This filtering ensured that the articles of research that are related but not directly relevant to the dissertation could be eliminated, meaning all the remaining articles would be relevant to the study. The PRISMA exclusion model was applied to illustrate the process and simultaneously create a comprehensive view. The PRISMA table is located on the next page. What follows is the list of relevant keywords that were used to retrieve the scholarly articles from the database. In the interests of keeping the data relevant to the contemporary period, the search range was set to the period of 2010–2019. This ensured that old, deprecated articles were not returned, because the information present within such articles may have been proven to be wrong, deprecated, or advanced in some way that rendered the articles moot or inaccurate (Moher et al., 2009).
Keywords | Year Range | |
UAE Internet Censorship, UAE social media censorship, Arab World Internet Censorship, Censorship in UAE | 2010–2019 | |
To enhance the organization of this paper, the data retrieved from the research articles are broken down into themes. These themes define not only the commonalities among the different scholars in terms of their research observations but also the specific areas that have been studied. This allows for a clear indication of what areas have been extensively explored and, inversely, which areas may require more attention and further investigation from future scholarly endeavors.
Hypothesis
Around the increasingly networked globe, social media is considered to be an essential part of interconnecting citizens and enabling people to engage and interact. The rapid growth and popularity of social networking sites (SNSs) have been attributed to the Web 2.0 trend involving the escalation of user-generated media as well as online collaboration (Shishkina and Issaev, 2018). With this in mind, this chapter explores previous studies on social media and censorship.
Social Media Usage Increase
According to Radcliffe and Lam (2018), since the event of the Arab Spring, the region in question has been undergoing an extensive process of digital and technological development. The rate of digital growth in this region is seen as being the highest in the world. Therefore, the usage of applications such as WhatsApp has grown considerably. There seems to be an increase in the number of different applications being used by the younger generation. It has also been observed that people in countries within the Gulf region have been forcing social media companies to turn their private user information over to them, citing security concerns. This provides evidence that social media platforms are being utilized at an extensive rate, which is progressively increasing with time (Howard et al., 2011).
Escalating Battle
Ghannam (2011) demonstrates that the Arab Spring and other such incidents have engendered significant fear among governments regarding what their citizens might do if given absolute free access to social media. Here, the author presents many different examples of governments cracking down on the free use of social media websites. Several cases are cited where people have used social media to publish something that the government found to be sufficiently insulting or degrading to warrant prosecution. Indeed, some of the people mentioned have been subjected to years in prison because of the views they expressed on social media. This demonstrates that some governments in the region are not willing to tolerate social media posts that criticize their regime or say anything that they consider insulting.
Young people have, as a response to this, taken steps to subvert the attempts of the government to take action against them based on social media posts. One of the most consistent usages of censorship in these countries is the usage of blacklisting websites by the ISPs under orders from the government. This involves blocking social media users’ access to their platforms and is executed in an attempt to black out all communication to eliminate any chance of information being posted that goes against a set narrative that the government may have. However, users have been actively bypassing these blocks, sometimes by simply switching to another social media platform (i.e. one that is not yet blocked by the government), or perhaps by extensively utilizing their familiarity with technology to use methods such as tunneling traffic through virtual private networks (VPNs) to bypass the governmental blocks (DeNardis, 2014).
Proxies have also been serving as a major tool that users have at their disposal to bypass governmental regulations and control over the Internet. It has been widely asserted that younger people are increasingly moving away from traditional media of information and discovery and are fulfilling their curiosity and information needs through interaction and communication on social media platforms instead. This demonstrates the importance of social media websites to younger individuals. The erosion of access to such platforms can thus be seen as depriving people of their means of communicating and expressing themselves to others. This represents a highly detrimental condition for the young people of the country, as they are subject to increasingly harsh laws and regulations that dictate how they can and cannot act. Their freedom of expression and ability to be completely honest is taken away, and they are deprived of it for fear of retaliation by the government (Jewels and Albon, 2011).
Overall, this has, in a sense, resulted in an arms race between the users of social media platforms and the government that seeks to control, limit, or eliminate access to them. The government and the users are continually in a race to devise ways to counteract the methods being employed by the other party. The government keeps trying to find a way to limit or block access to social media, while the users keep finding ways to bypass the restrictions of the government. The methods are continually evolving and changing over time (Deibert and Rohozinski, 2010).
Pillar of the Community
Wiest and Eltantawy (2012) investigated how the young adults of the UAE utilized communication technologies such as social media during a period that marked a great change in the Arab world, namely, the Arab Spring. Their paper emphasizes that young adults are a significant part of the population and that they are actively engaging with each other on social media platforms. The study analyzed the younger generation, demonstrating that almost all of them had access to devices that allowed them to browse these websites. Meanwhile, almost all the participants were users of at least one social media platform website. This demonstrates that social media usage accounts for a significant amount of interaction among individuals. This is especially pertinent in the case of individuals who did not generally have a direct connection before. The shift to a digital platform has allowed them to communicate more often and reliably as compared to enjoying occasional physical meetups.
The restriction of this service has several harmful effects on the young users of these platforms. One significant factor that can be observed immediately is the aspect of being silenced. The blackout of these platforms eliminates the possibility of communication occurring between countless parties. While some may reside close enough to each other for a physical communication session, a significant number of users would be too far away from each other to make meeting up feasible. This means that some can become largely silent about their associates, having had no other way of communicating with them beyond the social media link that they used to share. In general, the users of these platforms are extremely dismayed at the fact that the government has such a large amount of control over their communication platforms.
This sentiment is especially resonant among the younger generation of users, who feel like their individuality and creativity are being stifled by the older, more conservative, and less flexible generation (Correa et al., 2010).
This generational gap can often exacerbate the differences and misunderstandings that can occur between generations. Young people regard social media as a platform where they can express their honest opinions and views without being subject to the scrutiny that takes place in everyday physical interactions with people in general. So, social media represents a special space for them, one where they can express themselves more honestly and freely. The denial of access to these platforms, or the actions of the authorities who punish these individuals for going against the perception that the government wants to enforce, is largely seen as a propaganda- and brainwashing-based move (Myers and Sadaghiani, 2010). They also argue that the actions of the government are described as being predatory and executed in an attempt to promote social values and a general sense of ‘goodness’ (Myers and Sadaghiani, 2010).
As social media platforms represent a major pillar of communication to the younger generation, they see the restriction of it as comparable to being silenced or even, figuratively speaking, ‘having their tongue removed.
The methodology of any research endeavor can define the overall structure of the approach that will be utilized in the paper as well as the type of results that will be encountered.
Methodology
Each methodological approach possesses certain traits or characteristics that define its nature in terms of how the investigative endeavor is carried out.
Depending on the nature of the assignment and the resources available, choosing the most appropriate methodological approach can be the difference between effective research and a complete waste of resources and efforts. With all this in mind, this chapter describes the methodological approaches that were chosen for this dissertation (Kumar, 2019).
Approach
A combination of primary and secondary approaches was determined to be the most suitable approach for this topic. The primary approach involved utilizing a mixed interpretative approach aimed at extracting data from a closed-ended questionnaire (Appendix A). This allowed for the collection of data directly from the source, which would present strong corroborative evidence. The secondary approach also involved the use of a mixed methods approach, which consisted of using the data from scholarly articles as a means of providing additional context and information regarding the topic. A mixed approach was chosen because the research topic consists of an issue that cannot be completely studied to a satisfactory degree using only a quantitative or a qualitative approach. While a purely quantitative approach would provide statistical data and allow for the quantification of various parameters, it would, however, be simply limited to this aspect alone (Robson, 2011). That is, the data would be merely representative of the quantifiable factors associated with the investigation. It would thus fail to highlight the issues that cannot be quantified, and this would, in turn, decrease the overall effectiveness of the study. Omitting the qualitative aspects would exclude a very human factor upon which this study is based. A purely qualitative approach, meanwhile, would provide information in a purely subjective manner. The hard, quantifiable data that would be needed to measure the impact or provide trackable statistical data would be missing. This would lead to the data generated by the study being unusable for the tracking of trends and changes that occur within the social circles of the participants. Therefore, a combination of these two approaches was necessary in terms of allowing for the analysis of all the different aspects of this study (Brannen, 2017).
Furthermore, using both primary and secondary approaches allows for data to be gathered both directly and indirectly. The information retrieved from other scholars can then be compared with the data extracted from the primary approach as a means of obtaining corroborative evidence (i.e. substantiating the findings, or checking for discrepancies) (Clark, 2013).
Design
This sub-section explores the design of the research methodology. Specifically, the discrete methods utilized in the process of conducting this investigative exercise are discussed. The primary method employed consisted of a closed-ended questionnaire.
Questions that were pertinent to the topic were presented to the participants, who were given the option of replying using a closed-ended answering scale. The Likert scale was used to allow the participants to respond to the queries presented to them. This has several advantages, including, for example, the data collected from the participants will be quantifiable, which allows for the tracking of data, meaning it can then be interpreted for further use in the paper (Maxwell, 2012). As the participants did not have the option of providing open-ended answers, the data retrieved from them should be comprehensive and easy to process. Furthermore, the large variability in answers that can be derived from an open-ended questionnaire could be avoided, thus reducing the complexity of the data used in the dissertation.
Meanwhile, the second approach involved using electronic databases to search for relevant scholarly data in the form of articles. This introduced the work of other scholars into the dissertation, which we hoped would prove extremely useful. As the number of articles in the database was likely to be considerable, search criteria in terms of relevant keywords were applied to identify potentially relevant articles. These were then sorted and filtered as required to ensure that only pertinent articles directly related to the research topic remained. The research articles expanded the reach of the paper by providing additional data on aspects that could not be explored in this dissertation (Krosnick, 2018).
Both qualitative and quantitative data were made available from the research, which facilitated the comparisons among the data collected in the primary approach, meaning a more comprehensive overview of the research could be achieved. This represents a superior approach to limiting the research to a single method or approach.
Data Collection Method
This section describes the data collection methods used in the undertaking of this dissertation. Data collection tools are important aspects because they can be used to define the specific parameters within which the data collection is conducted. Therefore, it is always prudent to choose parameters that align with the aims and objectives of the dissertation. With this in mind, the age group deemed suitable for this topic was the 18– 21-year-old group. This group was chosen because the young people in this age group would be able to articulate their feelings about internet censorship and because they represent one of the most significant demographics in terms of using social media in the contemporary setting.
Meanwhile, a snowball approach was utilized to increase the number of participants taking part in answering the questionnaire. This ensured a sufficiently large sample size and allowed for a wide range of answers to be received (Johnson, 2012). The snowball approach comprises the use of referrals, where the initial users chosen to answer the questionnaires will forward it to parties related to them. This allows for the questionnaire to spread within similar social circles, thus increasing its exposure among
the individuals who fall within the chosen category. This primary data collection technique also presents the advantage of receiving answers directly from the users of social media who fall within a specific age range. A significant amount of empirical evidence will be the result of such an approach and the answers from this empirical or anecdotal evidence can then be compared to test the validity of each answer. This can be achieved through cross-analyzing the answers to check for discrepancies. The databases can provide a significant amount of insight through the secondary data collection method of extracting pertinent information from articles regarding the chosen topic. A secondary approach has the advantage of offering multiple perspectives on the topic from the investigations of others (Ghartey, 2014).
Data Collection Tools
This sub-section explains, analyses, and justifies the data collection tools selected for undertaking this study. Data collection tools have unique characteristics that separate one from the other. Each data collection tool relies on a specific approach to extracting data or information from the chosen field of investigation.
Accordingly, each data collection method will have a framework that may or may not fit into the requirements of the specific scholar. Ergo, a pertinent part of the selection of data collection tools is determining the most appropriate tool for the job in terms of fulfilling the standard requirements of the scholars in providing quality data.
Furthermore, the feasibility of using each tool must be taken into account, as some data collection tools have an approach that can involve a significant amount of financial resources (Spence, Lachlan, and Rainear, 2016).
Two data collection tools were employed in the process of fulfilling the goals of this dissertation. These were selected following substantial consideration of a significant number of factors. The feasibility of the chosen approaches was analyzed, and it was determined that the best tool for the primary approach was a closed-ended questionnaire. This was because a questionnaire would allow for the utilization of a more constructive and restrained approach and because, while an open-ended questionnaire would have resulted in a wide range of answers and quantifying them would have presented an arduous and unfeasible task, a closed-ended survey allows for the answers to be restrained to specific, measurable quantities.
Meanwhile, in terms of the second approach, exploring the literature of other scholars was determined to be the best approach (Rowley, 2014), largely because scholarly articles will have undergone extensive scrutiny and, correspondingly, they would provide a significant amount of reliably sourced and cited data that would increase the validity of this study. The possible presence of aspects not originally considered was also a major reason behind our choice.
Limitations
This sub-section presents the limitations of this work, which may affect the scope of the application of the results. All studies have inherent limitations as a result of their specific design and framework. This is because employing any approach presents certain characteristics and factors that may not always work to the benefit of the task being undertaken. Furthermore, the limitations of a study can be the consequences of having limited available resources for the investigative endeavor. The limited amount of resources can often result in research designs that have to be reduced in terms of ambition and scope and, subsequently, the methods that can be utilized. Per se, the shortcomings of this study are also inherently based on its design (Shipman, 2014).
One of the limiting factors associated with the approach selected concerns the usage of a closed-ended questionnaire. This is because when participants’ answers are reduced to a series of choices that may suffer from large, overlapping gaps, it can be difficult to obtain any nuanced data. The aspect of transferring such a subjective, qualitative factor as human thought and emotion into a quantifiable, objective measure presents significant challenges. One such problem is that not everyone will have the same rating on the scale, that is, people may have their scales in terms of how they evaluate items. Like this, the lack of a standard scale to measure the participants’ responses can diminish the elemental data from the qualitative side. In short, the questionnaire cannot be used to elicit specific and individual responses, which could each provide a unique perspective on the subject (Christensen, Johnson, and Turner 2011).
The secondary approach of utilizing the articles of other scholars as a means of increasing the available information for this dissertation also entails certain limitations. The secondary approach means that work can only be done on previously extracted data. Thus, all that can be done is to review the paper and interpret the data, meaning no new aspects can be uncovered using this approach (Terrell, 2012).
It is important to note that limitations also lie in the inability to access a larger number of participants for the questionnaire. This may have increased the risk of sampling bias, where the presence of a unique phenomenon may give the impression that such activity occurs in the environment being analyzed. There may also be a language gap, as not everyone involved is fluent in English. For this reason, some of the participants in the study may have misinterpreted the questions provided. Unfortunately, this limitation could not be overcome due to the limitations in terms of available resources.
Results
This section presents the results extracted by following the methodology outlined above for gathering the data for the investigative endeavor. First, the results of the questionnaire, which involved the participation of young people aged between 18 and 21, are presented. Only the data and the trends that can be analyzed through the results are described here, while the data trends are compared as a means of self-correcting any possible errors or contradictions that may have arisen, through a process of cross-checking to ensure that everything is corroborative. Each variable is presented individually.
The secondary approach data is presented in a mixed interpretative fashion, as some of the aspects that are explored in the articles will not be specifically limited to quantifiable data. Including quantifiable data is hugely important to the determination of trends and pattern recognition, while it does exclude aspects that cannot be quantified for lack of an available method to measure them accurately. From this perspective, a mixed data representation method of presenting results was employed, as it can more effectively capture the intricacies and the quantifiable factors of the chosen studies for analysis (Major and Savin-Baden, 2013
First, the data from the primary approach is laid out, while the entire results and the questionnaire itself can be found in Appendix A. As can be seen from the first question, almost all the survey respondents utilize social media. Although a few of the participants do not seem to use it as regularly as the users in the highest cohort and a few even have a neutral attitude toward social media, the overall result is indicative of social media usage being common among youths. Once again, in line with the previous question, a large cohort of the participants strongly agreed that the government was trying to censor social media. Almost the entire cohort of participants strongly agreed that the government’s action of censoring social media had led them to alter their communication methods and habits.
The entire group agreed that the blocks that had been imposed on users as a result of the government instructing ISPs to blacklist platforms that the government deemed offensive were not only circumventable but that they were all able to circumvent the blocks. Most of the cohort strongly disagreed with the government’s censorship and thought that what the government was doing by censoring and blocking social media sites was wrong, while a few might have had some doubts, with others perhaps even partially agreeing with the attendant motive. The last question consisted of asking the group if they were able to express themselves freely. While most strongly disagreed, there were a few who did not perceive it in that way, while some remained neutral about the issue.
Censorship has affected how young users are now connecting to the Internet. However, they have several ways to mask their activity and avoid persecution by the government. This demonstrates that the users will continue to use social media platforms by using means to mask their activities, even under the threat of legal action from the government. The younger generation also finds the older generations to be less flexible and unlikely to adopt the usage of social media in their regular day-to-day lives. The users expressed that they would be in extreme distress if they were denied social media access, stating that individuals are primarily responsible for what they expose themselves to.
Next, the data from the second approach, which uses scholarly articles, is presented. It was noted that the majority of the users of the platforms generally did not like the idea that their posts would be subject to great scrutiny by the government. The idea of having to consistently monitor their speech and how they behave is regarded by the younger users of social media as a serious form of oppression. A significant number of social media platforms allow users to have blogs. This is where they can share their thoughts and feelings with fellow users, form solidarity bonds, and discuss interesting subjects. When there is an omnipresent governmental threat, where the users cannot be entirely sure which of their posts might be deemed unsuitable material, a certain amount of confusion and fear ensues (Warf, 2011).
Zittrain et al. (2017) demonstrate that within the region of UAE, a large part of the censorship consists of religious-based filtering. That is, content that is perceived to be offensive or derogatory toward the religion of Islam is blocked and/or censored. This extreme reaction, allegedly taken in the name of safeguarding religion, is cited as being entrenched in the fact that the region is heavily influenced by Islam. For certain, the population of the area is predominantly Muslim, including the ex-pats, who constitute a large part of the population many of whom originate from similar faith-based and religion-focused Muslim countries. Even websites that have not been directly offensive to the government or the religion of Islam have fallen victim to the filtering process.
Content promoting other religions or even providing information about them has also been filtered by the government.
It is stated that the government is heavy-handed in terms of controlling the type of content that UAE residents can be exposed to. The extreme filtering parameters and
the potentially harsh and extensive sentences and punishments that could be faced by offenders are cited as signs of extreme intolerance and a lack of openness to outside cultures and ideas. Here, Joseph (2012) demonstrates that social media platforms have helped revolutionaries to communicate with each other and plan their tactics in countries where the oppressive regime of the government has reached intolerable levels. This is presented as one of the areas that a government wishing to avoid a potential revolt against its regime would be interested in. The UAE, in continuing to employ a government ruled by royalty, is, as this paper shows, a potential target for a repeat of what happened in the Arab Spring.
It is speculated, however, that, in some cases, the usage of social media sites may also be preventing people from revolting. This is because they are generally placated due to the content they browse online. Indeed, it is highlighted that a large number of users partake in consuming content that is generally intended to make them feel calm and content. This prevents their curiosity from rising to the point where they may relate to or investigate the potential for taking action against the government, which is in line with the activity of filtering that the government carries out regularly. This is especially prevalent in the case of religious content. In short, the government can effectively carry out mass censorship due to the shared beliefs of a large number of Muslim residents, which means it does not go against the sensibilities of the local population.
Subramanian (2011) demonstrates that the governments of Middle Eastern countries, including the UAE, have taken steps to ensure that the telecommunication companies need the approval of the government to operate. The ISPs in the UAE consist of a national monopoly involving the Etisalat Company, with Du being the second telecommunications provider, albeit with a very limited number of users. The government has chosen to filter the content that is exposed to the population by removing any that it deems potentially ‘harmful’ to individuals. The actual harm is not explained or described in any manner and is perceived as being religion-based due to the nature of the country's government.
Discussion
The interpretation of results is an important component of any scientific investigation. Interpretation involves taking the results of the research endeavor and then analyzing the relevant data. This analysis can then be used to interpret different perspectives derived through using the data from the experiment as a seed to project how the data can be applied to the current field of knowledge. This is a vital component because data are not inherently useful; rather, a dataset needs to be placed into a certain context to provide it with the meaning that can then be used to understand what the data represents. This also opens up the possibility of one datum having several connotations or meanings that can be derived from the same variable or piece of information. This prevents the situation where certain factors of a topic can have a multitude of dimensions that all need to be explored, analyzed, and understood to achieve a complete systematic understanding of the topic.
Hence, interpreting data can further demonstrate which perspectives have been considered based on the research data. This illustrates which aspects have received considerable attention and which have not received as much. Furthermore, unknown perspectives can often be identified by comparing a list of known perspectives to see if such elements have been addressed previously. As interpretations can be highly subjective, and as certain qualitative elements are used to interpret the data, it is important to note that the interpretations of the data presented here may not represent the entirety of what can be extracted. Therefore, it would be prudent for other scholars or interested individuals to undertake the effort to try and form their perspectives on the data presented in this paper (Meyers, Gamst, and Guarino, 2016).
One of the details that emerged from the questionnaire examples that were provided to the young users of the social media platforms was that the users regularly utilized social media platforms. Almost all of them use social media, and for them, it forms a significant part of their daily routine. This demonstrates that the role of social media has evolved from being simply a way of communicating with different individuals to being a vital part of everyday life, where the communicative ability to reach remote users has become a ubiquitous part of life. This is pertinent because these users, being of a young age, adopted this technology at such an early point in their lives that any usage restrictions imposed on the platforms could be hugely detrimental to their ability to communicate with their friends (Deuze, 2011). It may even take a psychological toll on them, similar to what occurs when a person is isolated and not allowed to interact with other people socially. The effect, in the end, would be the same, as the users would be effectively silenced.
While the majority of the users agreed with the notion that the government is trying to censor social media platforms, others, who were not as sure, exhibited general confusion. This could be a result of their religious beliefs, which may have influenced the answers of some of the participants in the questionnaire (Gerbaudo, 2013).
It is important to note that this very faith-based system is the major driving force behind the government’s decision to take such a harsh stance on what is approved for online viewing and what is considered inappropriate. The way people communicate has been greatly affected by the censorship imposed by the government on social media, which was evident from the fact that almost all the users strongly agreed with what was suggested in the related question. While a very small minority disagreed here, this may, again, have been a result of their considering the possibility that they may be sinning while participating in the survey. Indeed, this is most likely the case, given the answers that were provided in the previous questions (Coulson, 2017).
Interestingly, it would appear that all the users who were surveyed for this investigation had the technical capability and knew how to circumvent whatever blockage techniques the government used on the social media platforms that they utilize. The entire group answering yes to this question demonstrates that some of the previously answered questions involved a level of hesitancy about this circumvention, as those who remained unaffected by social media censorships or blockages would not likely be seeking ways to circumvent them. Of course, while there may be the occasional user who is interested in technology and in tinkering with computers, the average user will not seek out such topics unless they are prompted to do so by a specific event, such as the blockage of their social media platform (Ernest et al., 2014).
Most of the users agreed that the government was wrong to censor content. This question was asked in terms of censorship in general and while it included social media, it did not explicitly mention it. This meant that the question was related to censorship as a whole, specifically when applied by the government of the UAE. For the most part, the users strongly disagreed with the stance that the government has taken against allegedly questionable content, as the content the government disapproves of can be highly variable, depending on their agenda. Some of the users did not agree in such strong terms, while others remained neutral here. This further illustrates the effect of censorship on the behavior of the people in the sense that as some people are worried that they may be identified through the views they hold, they sometimes deviate toward the other side rather than agree with the idea of government wrongdoing (Warf, 2013).
The next question was almost in complete alignment with the previous one in terms of the results that were returned. There was little change beyond five percent of the answers being taken from neutral to disagree. The answer to this question of expression demonstrates that the content these people desire to consume has been largely determined by the government to be harmful or offensive. Since some users were unable to express their views, this is indicative of the fact that openly stating views that may be seen as running counter to the religion of Islam or that of the country can involve severe punishments as a consequence. The government has, in effect, silenced a large segment of the population from speaking out against its policies through the threat of legal action (Alqudsi-ghagra, Al-Bannai, and Al-Bahrani, 2011).
Most of the participants answered that they would experience distress if social media were cut off, which demonstrates the incredible amount of social interconnectivity that these social media platforms represent. Meanwhile, the idea that the government is spying on the people is universally hated by all the participants. The users surveyed almost all the visited content that was blocked by the government, which indicates the users of these platforms generally have little regard for the internet laws and the attendant regulations of the country. The older generation was also seen as being less in line with the vision that the younger generation had in mind. This clash of expectations can be seen as one of the issues that cause government officials to create rules and regulations for a generation of people they do not fully understand.
One of the most problematic aspects relates to the fact that the laws that define the regulations and rules regarding internet usage are extremely vague in terms of meaning. This vagueness leaves the laws open to a very wide range of interpretations. These interpretations can then be used as an excuse to exercise the force of the law in an unlawful and unethical manner. This abuse of the law prevents a large segment of the population from being able to effectively speak out about the issue or create any awareness about it in the first place. A lack of awareness leads to social problems being largely ignored or kept as an open secret, as the information that is pertinent to specific cases will not be available if it is seen as potentially offensive or generally unacceptable by the country. For this reason, an awareness of the issue cannot be created, which may lead to a successful protest by the people to create change (Rajan, Ravikumar, and Al Shaer, 2017).
The ability to communicate represents a vital factor in how well people can effectively cooperate to accomplish whatever mutual goal they may have. Such cooperation can occur only when people can communicate their situations to each other effectively, exchange ideas, engage in discussions, or communicate in general terms. Any severance of the communication lines leaves the individual participants unable to counter the superior resources that are available to the government. This has been recognized by many governments and has been used as a tactic in politically sensitive times where the country and its reputation were in question. The various revolts of the people that might otherwise have arisen have been pre-emptively thwarted in a move by governments hoping to quell the flow of information, both into and out of the country, among unauthorized people (Szajkowski, 2011).
These moves are often deliberately aimed at severing the modes of communication of the people in an attempt to weaken the organizational behavior displayed by those supposedly participating in revolts. As is evident from the secondary results, scholars have illustrated that the UAE is heavily focused on determining filter parameters by utilizing a religious-based system. Therefore, the content that is heavily targeted and filtered out is any material that represents an anti-Islamic stance or is harmful according to the teachings of Islam. This has been used as a precedent to block other websites as well. Indeed, generally speaking, there has been massive abuse of vague laws regarding cybercrime, cyberbullying, or internet use in general. This means that users of social media face the risk of being subject to legal actions if they fail to comply with the standards that the government has deemed ethically and morally correct (Bowe and Blom, 2010).
Associated fears have led to several users transitioning to more anonymous means of communication and even subverting the government’s blocks by using services such as virtual private networks (VPNs). VPNs have become a major software tool regularly utilized by citizens of countries such as the UAE so that they can browse the content that the government has deemed too dangerous for them. This is indicative of the fact that there is an enormous breakdown in communication between the government officials taking these actions and the ordinary citizens trying to access content in the face of governmental pressure. The wide range of people who have become aware of technologies that can be used to bypass governmental blocks has increased significantly. This increase can be attributed to the fact that regular users, when unable to access their regular content, became interested in the technical concepts underlying what was happening (Al Sakkaf and Baker, 2018). From there, they began to learn more about the issue and eventually realized there were several ways in which people could bypass governmental restrictions on internet usage. This led them to utilize these ways before forwarding the information to their friends, creating a chain of people who suddenly possessed the technical capability and know-how to bypass the efforts of the government. This has the potential of rendering the governmental blacklisting merely ceremonial (Vora, 2012).
From these results, it can be determined that the governmental blocking and censorship of websites is largely despised by the users of such websites. It has triggered many of them to discover ways of circumventing the governmental blocks before proceeding to access the blacklisted content anyway, rendering the entire exercise by the government largely redundant. This lack of communication between the government and the people represents a strong point of friction that may be having detrimental effects on the possibility of cooperating and reaching a compromise.
Conclusion
This section consists of the concluding part of this work. The section is presented under several different headings based on the information presented thus far in the dissertation. Each different element is presented. First, the summary sub-section presents a summarisation of the data that was presented in the paper. This is followed by the sub-section on the key findings. These key findings consist of the vital interpretations and perspectives that could be derived from the available data. Both quantitative and qualitative perspectives are provided to increase the comprehensibility of the presented information and to cover as many dimensions as possible within the feasibility of the paper.
Summary
This sub-section presents a summary of each of the previous chapters presented above. The summarization of the entire dissertation serves the purpose of breaking down all the information as a means of increasing the comprehensibility of the paper and providing an extra level of organization. Furthermore, a synthesis of the different information that was presented in the paper is carried out as a means of achieving an understanding greater than the sum of its parts. The information that can be gleaned from each of the previous chapters is presented here in chronological order.
The first chapter, the introduction, commenced the paper by providing a brief outline of the nature of the Internet and its use in the context of modern society. It demonstrated that while social media usage is a huge part of the way people communicate, it has been facing certain restrictions due to the different beliefs and perceptions of people around the globe. The chapter also outlined the aims and objectives of the paper and provided the rationale behind undertaking the investigation. An outline of the entire paper was also provided to ensure ease of navigation and to improve the organizational layout of the paper and the way it presents information. The ethical considerations that could be associated with the project were analyzed in great detail to ensure that standard ethical violations would not occur in either the primary or the secondary research applied in the dissertation.
The second chapter, the literature review, provided the rationale behind consulting scholarly articles as a means of not only providing context to the subject area being investigated but also improving the research design. The data extracted from the articles were used as a means of providing context to the research in terms of where it stood about the investigative endeavors previously undertaken by other scholars. The different databases searched yielded several results, which provided the additional data necessary to develop a more enlightened, better-informed perspective on the subject under investigation. Furthermore, some perspectives not previously considered were encountered and these served to increase the comprehension and reach of the project.
The third chapter consisted of laying out the methodology used in the investigative endeavor that was outlined in the first chapter. This chapter demonstrated that the best means of investigation, given the resources of the dissertation, would involve using a combination of primary and secondary approaches. This allowed for the extracted data to originate from two different categories of sources. The first consisted of the social media platform users under investigation, with this direct access to the subject of the project’s focus creating the potential for achieving greater insight into the users’ cognitive framework. Meanwhile, the second category was the secondary sources that formed the secondary approach deemed the best method for providing additional context and insight into any nuances and perspectives that might not have been considered before.
The fourth chapter consisted of the results that were obtained as a result of carrying out the methodologies that were listed in the previous chapter. The results consisted of the responses that were elicited from the users of the social media platforms (i.e. the data generated using the primary approach method) and the second dataset that was extracted from scholarly articles about the subject of the research. These articles represented works of investigation completed by other scholars who were interested in similar elements and who were invaluable not only in terms of providing corroborative evidence for the information in this dissertation but also in terms of inspiring suggestions and recommendations regarding what could have been achieved to a higher standard.
Meanwhile, the fifth chapter presented the discussion. This discussion was based on the information that was retrieved in the previous chapter and took elements of all the data that were presented in the previous section and used this as a means of synthesizing all the information available. This synthesis of information serves to create an understanding of the topic that is intended to be greater than the sum of its parts. The data from the primary survey served to substantiate many of the findings that were extracted from the articles of other scholars. Specifically, here, a universal dislike of governmental interference was observed. In short, users are not fond of the idea that the government has the power to punish them for posting content on the Internet that could potentially be perceived as a violation of the laws of the country and could leave them open to prosecution.
It was also demonstrated that the UAE has vague laws related to the use of digital platforms and social media in general. This is potentially seen as a way for the country to abuse its power by instituting a law guideline system that is highly subject to interpretation and can be easily abused by those in power.
The sixth and final chapter, which this summary forms part of, is composed of a summary of the entire dissertation followed by the key findings of the investigative endeavor, which are presented to highlight the major discoveries that partially represent the potential of internet usage in the academic environment. The social and academic contributions that this dissertation could make are enumerated to signify the importance of the outcomes of this study, while the limitations of this dissertation, based primarily on its inherent design, are also described. Finally, recommendations on how this project can be improved upon by other scholars are presented to act as a guide and reference point for future research.
Key Findings
The key findings of a dissertation represent one of the most important aspects of any research study and are the most significant results achieved through executing an investigative endeavor. They represent some of the most important elements derived from the research material, which can then be presented in terms of justification. This justification relates to the time and other resources that were consumed as a result of undertaking the endeavor. From these key findings, potential contributions – with the findings serving as the inspiration or main concept – can be created. With this in mind, the key findings are explored in the following sub-section.
It was discovered that young users of social media platforms were unhappy to discover that their access to their favorite platforms had been denied. This led them to discover other ways of trying to access the websites or platforms, which eventually allowed them to bypass the blocks and digital blockades that had been established by the government. Such user behavior could have been avoided if the government had not, it could be argued, overreacted in the first place, since this was responsible for triggering the indignation of the users in the first place; indignation that led them to completely disregard the rules that the government had implemented. There is further corroborative evidence that the content that the UAE may be filtering out may not be as offensive or as filled with hate speech as the authorities would have us believe.
As the rules are at least partially based on a specific religious ideology, a majority of the rulings are also made on a religious basis. As is often the case with religious-based logical application, the result has been the condemnation of material that did not
even contain anything particularly offensive. This total overreaction to what is perceived to be an insult or sin generally emerged as a common theme in the findings.
Social and Academic Contributions
Whenever such a significant research endeavor is carried out, the results derived from it can have many potential uses. This sub-section of the dissertation presents the potential academic contribution that has been or will be made, through the information that has become known as a result of carrying out the research endeavors associated with this dissertation. Social and academic contributions represent some of the most significant reasons for carrying out investigative research. The collected aggregate, or sum of knowledge from different scholars, contributes to social and academic development by introducing new knowledge into the field, which may be used for a variety of purposes as needed. In general, it increases the quality of life in contemporary society as a whole.
This dissertation provided a considerable amount of insight into the usage of social media within the Middle Eastern country of the UAE. The sociological understanding of UAE residents has been enhanced, as their mentality about the subject has provided insight into how the younger generations are more open to social media than the older, ruling generations. In academic terms, it was shown that the users of these services – which are intended to facilitate free speech – are, in fact, not capable of speaking freely, because a UAE resident found guilty of posting something deemed as offensive can be subjected to harsh punishment.
Limitations of the Study
Every study will inevitably be subject to several limitations that will be the result of both the factors that are under the control of the researcher and those that can be controlled only partially or not at all by the researcher. The most common limitations pertain to the resources available for conducting the research. Limited resources naturally restrict the courses of action that can be taken to alleviate any problems, while the more ambitious aspects of the project can become unfeasible. This can result in settling for a potentially less robust method of conducting the study that could, in turn, reduce the quality of the results produced.
This section presents the limitations that pervaded this dissertation. These limitations represented some of the reasons why certain methods that could have theoretically been employed could not be considered. One such limitation concerned the lack of available physical databases for exploration. Physical databases may contain valuable supplementary information about the subject, perhaps providing potentially unique insight, while not every article can be published in a digital format, nor can every article be made available online for everyone to examine.
The closed-ended style survey also presented an important limiting factor. As the responses of the test subjects were significantly limited, a more binary representation was found in the data derived from them. The inability to take a more qualitative approach by asking the participants more open-ended questions resulted in greatly pared-down answers that failed to convey the nuances of thought that would perhaps have accompanied them. Each participant would have presented their reasons for their specific answers and, thus, new insights could have been identified and explored. However, due to the closed-ended design, such insights were completely lost in translation.
Meanwhile, the study of the work of other scholars in the second approach was limited by the age range that was chosen for the primary approach in this dissertation. In short, the age range of 18 to 21 years of age does not represent a well-defined age range in terms of social media users. Subsequently, the small number of studies that incorporated this exact criterion led to further issues.
Recommendations for Future Research
This sub-section provides several recommendations that other scholars can consider to increase the depth of investigation that has been conducted on this topic thus far. The recommendations were generated based on the information that was presented in this paper. Here, based on what could be gleaned, several observations were made. From these observations, recommendations that could resolve some of the issues associated with the investigation conducted in this dissertation are presented. In addition, any improvements that could have been made to the overall research in terms of design or framework are presented to show how this investigative endeavor could have been improved.
One change that would have greatly improved the study overall in terms of the primary approach would have involved the utilization of an open-ended questionnaire. An open-ended questionnaire would have allowed the participants to discretely convey their answers and provide the context that would be required for a better understanding. With this, potential new aspects that this dissertation did not consider may have been
revealed, which could have potentially expanded the range and scope of the research to provide a more comprehensive overview of the topic.
Furthermore, when selecting the data from the scholarly articles, a lack of access to certain articles locked behind paywalls, or other such restrictive means that require significant funds, limited the scope of the articles that could be utilized in the study. The lack of access to certain scholarly articles meant that information that could have been highly pertinent to this study was missing and left uninvestigated. For this reason, there are certain gaps in the knowledge base provided by this dissertation. Having access to a larger library, or a larger number of scholarly articles will greatly increase the range of information available for utilization in the second approach.
Below is the bibliography cited in the study.
Bibliography
Al Sakkaf, F. and Baker, S. 2018. Legalities of using virtual private networks. Ct.
Uncourt, 5, p.10.
Al-Jenaibi, B.N.A. 2011. Use of social media in the United Arab Emirates: An initial study. European Journal of Social Sciences 23(1)
Alqudsi-ghabra, T.M., Al-Bannai, T. and Al-Bahrani, M. 2011. The Internet in the Arab Gulf Cooperation Council (AGCC): Vehicle of change. International Journal of Internet Science, 6(1).
Bowe, B.J. and Blom, R. 2010. Facilitating dissent: the ethical implications of political organizing via social media. Politics, Culture & Socialization, 1(4), p.323.
Brannen, J. 2017. Mixing methods: Qualitative and quantitative research. Routledge.
Christensen, L.B., Johnson, B., Turner, L.A. and Christensen, L.B. 2011. Research methods, design, and analysis. Pearson Education.
Clark, G. 2013. Secondary data. In Martin, D & Flowerdew, RTN (eds.). Methods in Human Geography (p.57). Pearson Education.
Connelly, L.M. 2014. Ethical considerations in research studies. Medsurg Nursing, 23(1), pp.54-56.
Correa, T., Hinsley, A.W. and De Zuniga, H.G. 2010. Who interacts on the Web? The intersection of users’ personality and social media use. Computers in Human Behavior, 26(2), pp.247-253.
Coulson, N. 2017. A history of Islamic law. Routledge.
Deibert, R. and Rohozinski, R. 2010. Cyber wars. Index on Censorship, 39(1), pp.79-90. DeNardis, L. 2014. The global war for internet governance. Yale University Press.
Deneulin, S. 2014. Wellbeing, justice, and development ethics. Routledge.
Dennis, E., Martin, J. and Woods R. 2016. Media use in the Middle East 2017: A seven-nation survey. Available at: https://www.researchgate.net/publication/328542247_MEDIA_USE_IN_THE_MI DDLE_EAST_2017_A_Seven-Nation_Survey_monograph
Deuze, M. 2011. Media life. Media, Culture & Society, 33(1), pp.137-148.
Ernest, J.M., Causey, C., Newton, A.B., Sharkins, K., Summerlin, J. and Albaiz, N.
- Extending the global dialogue about media, technology, screen time, and young children. Childhood Education, 90(3), pp.182-191.
Fink, A. 2019. Conducting research literature reviews: From the Internet to paper. Sage Publications.
Freedom House. (2018). The UAE. Available at: https://freedomhouse.org/report/freedom-world/2018/united-arab-emirates
Galvan, J.L. and Galvan, M.C. 2017. Writing literature reviews: A guide for students of the social and behavioral sciences. Routledge.
Gerbaudo, P. 2013. The ‘Kill Switch’ as ‘Suicide Switch’: Mobilizing side effects of Mubarak’s communication blackout. Westminster Papers in Communication and Culture, 9(2).
Ghannam, J. 2011. Social media in the Arab World: Leading up to the uprisings of 2011. Center For International Media Assistance, 3(1), pp.1-44.
Ghartey, F. 2014. Research methods. Central University Library.
Howard, P.N., Duffy, A., Freelon, D., Hussain, M.M., Mari, W. and Maziad, M. 2011. Opening closed regimes: What was the role of social media during the Arab Spring? Available at: SSRN 2595096: http://dx.doi.org/10.2139/ssrn.2595096.
Jewels, T. and Albon, R. 2011. Reconciling culture and digital literacy in the United Arab Emirates. International Journal of Digital Literacy and Digital Competence (IJDLDC), 2(2), pp.27-39.
Johnson, A.P. 2012. A short guide to action research. Pearson Education
Joseph, S. 2012. Social media, human rights, and political change. Human Rights and Political Change (June 2, 2011): Boston College International & Comparative Law Review, 35, p.145.
Katzman, K. 2010. United Arab Emirates (UAE): Issues for US Policy. DIANE Publishing.
Krosnick, J.A. 2018. Questionnaire design. In The Palgrave Handbook of Survey Research (pp. 439-455). Palgrave Macmillan, Cham.
Kumar, R. 2019. Research methodology: A step-by-step guide for beginners. Sage Publications Limited.
Loader, B.D., Vromen, A. and Xenos, M.A. 2014. The networked young citizen: Social media, political participation, and civic engagement. Information, Communication & Society, 17(2), pp.143-150.
Major, C.H., and Savin-Baden, M. 2013. Qualitative research: The essential guide to theory and practice. New York, NY: Routledge.
Maxwell, J.A. 2012. Qualitative research design: An interactive approach (Vol. 41).
Sage Publications.
McMenemy, D. 2012. Emergent digital services in public libraries: A domain study. New Library World, 113(11/12), pp.507-527.
Meyers, L.S., Gamst, G. and Guarino, A.J. 2016. Applied multivariate research: Design and interpretation. Sage Publications.
Miller, T., Birch, M., Mauthner, M. and Jessop, J. (eds.). 2012. Ethics in qualitative research. Sage Publications.
Moher, D., Liberati, A., Tetzlaff, J.A.D. and Altman, D. 2009. PRISMA 2009 flow diagram. The PRISMA Statement, 6, p.1000097.
Myers, K.K. and Sadaghiani, K. 2010. Millennials in the workplace: A communication perspective on millennials’ organizational relationships and performance. Journal of Business and Psychology, 25(2), pp.225-238.
Neuman, W.L. and Robson, K. 2014. Basics of social research. Toronto: Pearson Canada.
Radcliffe, D. and Lam, A. 2018. Social media in the Middle East: The story of 2017. Available at: SSRN 3124077/.
https://damianradcliffe.wordpress.com/2018/02/15/white-paper-social-media-in- the-middle-east-the-story-of-2017/
Rajan, A.V., Ravikumar, R. and Al Shaer, M. 2017. UAE cybercrime law and cybercrimes: An analysis. In 2017 International Conference on Cyber Security and Protection of Digital Services (Cyber Security) (pp. 1-6). IEEE.
Resnik, D.B. 2011. What is ethics in research & why is it important? National Institute of Environmental Health Sciences, 1(10).
Robson, C. 2011. Real-world research (Vol. 3). Chichester: Wiley.
Rowley, J. 2014. Designing and using research questionnaires. Management Research Review, 37(3), pp.308-330.
Russell, B. 2013. Human society in ethics and politics. Routledge. Shipman, M.D. 2014. The limitations of social research. Routledge.
Shishkina, A. and Issaev, L. .2018. Internet censorship in Arab countries: Religious and moral aspects. Laboratory for Monitoring of Sociopolitical Destabilization Risks, National Research University Higher School of Economics, Moscow.
Spence, P.R., Lachlan, K.A. and Rainear, A.M. 2016. Social media and crisis research: Data collection and directions. Computers in Human Behavior, 54, pp.667-672.
Subramanian, R. 2011. The growth of global internet censorship and circumvention: A survey. Communications of the International Information Management Association (CIIMA), 11(2).
Szajkowski, B. 2011. Social media tools and the Arab revolts. Alternatif Politika, 3(3), p.420.
Terrell, S.R. 2012. Mixed-methods research methodologies. The Qualitative Report, 17(1), pp.254-280.
Vainio, A. 2013. Beyond research ethics: Anonymity as ‘ontology’, ‘analysis’ and ‘independence’. Qualitative Research, 13(6), pp.685-698.
Vora, N. 2012. Free speech and civil discourse: Producing expats, locals, and migrants in the UAE English-language blogosphere. Journal of the Royal Anthropological Institute, 18(4), pp.787-807.
Warf, B. 2011. Geographies of global internet censorship. GeoJournal, 76(1), pp.1-23.
Warf, B. 2013. Global Internet censorship. In Global Geographies of the Internet (pp.45-75). Springer, Dordrecht.
Wiest, J.B. and Eltantawy, N. 2012. Social media use among UAE college students one year after the Arab Spring. Journal of Arab & Muslim Media Research, 5(3), pp.209-226.
Zittrain, J.L., Faris, R., Noman, H., Clark, J., Tilton, C. and Morrison-Westphal, R. 2017.
The shifting landscape of global internet censorship. Available at: https://dash.harvard.edu/bitstream/handle/1/33084425/The%20Shifting%20Land scape%20of%20Global%20Internet%20Censorship-
%20Internet%20Monitor%
Get 3+ Free Dissertation Topics within 24 hours?